Education K-12
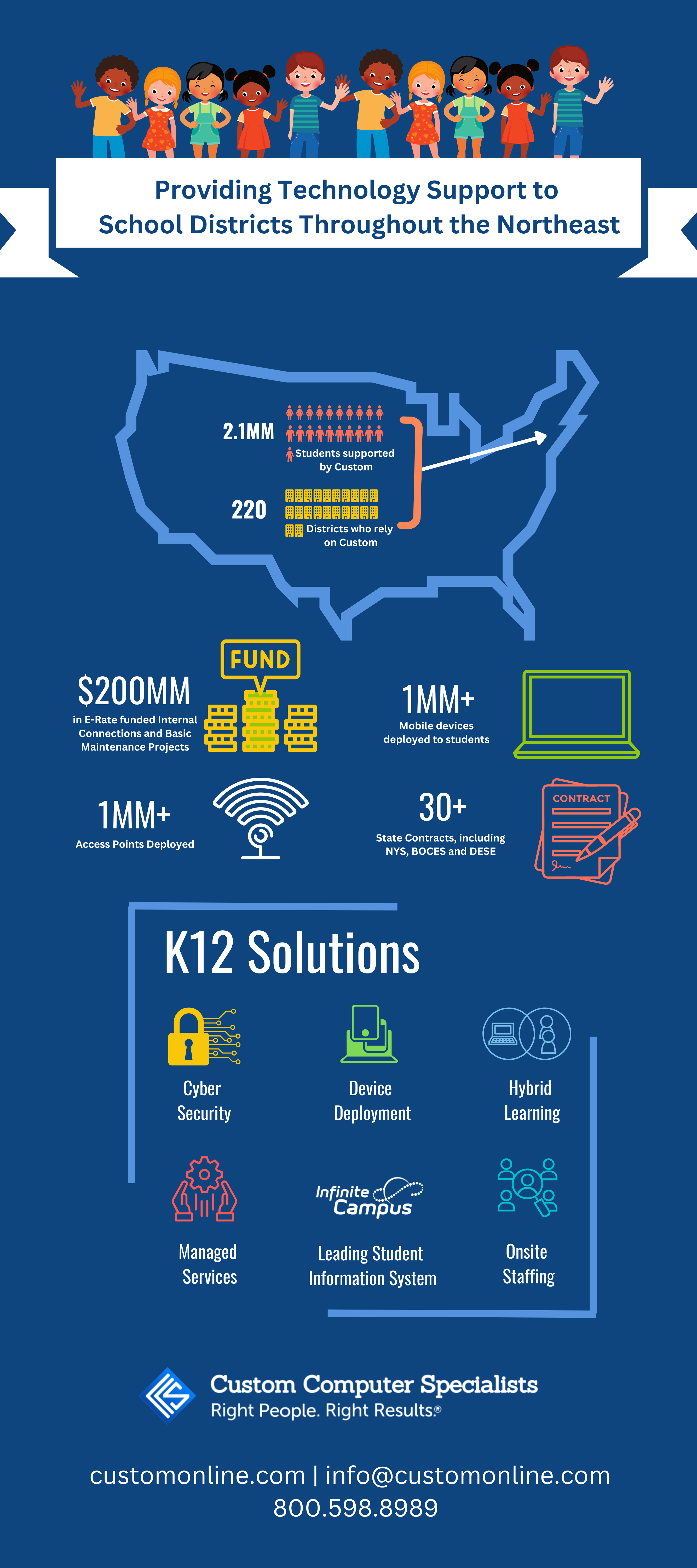
IndustriesWe provide technology support to over 200 school districts throughout the Northeast. Specializing in E-Rate funding, onsite staffing and physical and data security solutions we focus on improving student learning outcomes, while creating an end user experience that exceeds expectations.
Within the past few years, the definition of a “classroom” has broadened and evolved. The need to educate in school, as well as the home, introduced new process and technology challenges for faculty, students and parents. Accommodating time-constrained and/or geographically distant students, and hose with disabilities has become the new normal for educational institutions—especially while supporting expanding business goals and evolving student expectations.
K12 Solutions
Our K12 Solustions support students, faculty and administration, ensuring an end user experience that meets or exceeds expectations. Whether it’s Cyber Security, Device Deployment, Onsite Staffing or Managed Services you can rest assured that the Custom team will successfully deliver on our committments.
Hybrid Classroom Solution
Whether a student is in the classroom or learning from home, our turn-key solution was designed for today’s blended learning environment. With speaker- and presenter- tracking cameras, dual displays, wireless sharing, and sophisticated audio, our CustomClassroom Kit keeps students engaged regardless of their location.
Help Desk for Students, Teachers and Parents
Say goodbye to students missing classes or homework assignments due to technical issues. Our CustomHelpDesk for Education is staffed with experts who resolve technical problems specifically associated with learning from home. We have helped many school districts accelerate their push into distance and HyFlex learning by providing support models that assist both students and their parents.
K-12 and higher education institutions turn to Custom to expand their student body and provide a higher-quality hybrid learning experience for students and faculty.
Supporting School Districts
Today’s digital native students are born into an age where technology is pervasive. Their interactions with digital devices and applications begin at an early age. It’s not surprising then, that schools are shifting their traditional teaching tools from books to electronic devices, from chalkboards to interactive whiteboards – implementing technology to foster learning with greater impact. But integrating these technology resources can be challenging. At Custom Computer Specialists, we understand the importance of our children and the future of our country. With that in mind, we always make sure while we are helping to solve our customer opportunities, we are continuing to educate ourselves on the needs of the Education sector and the demand on the system to provide the best possible solution.
A Partner with the Right Credentials
Custom provides technology support and education consulting services and products to more than 400 school districts in the Northeast and across the US. We support more than 150 districts with our specialists working onsite on a daily basis. And we spearheaded one of the largest K-12 wireless projects in the US.
Rooted deeply in the education community, our dedicated education specialists regularly attend national conferences, including ISTE and USAC, to gain knowledge and updates that we take back to our regional customers. Custom and our team of specialists are members in a number of local, state and national K-12 education associations.
Custom holds a number of local and state contracts, making it easy for you to do business with us. We are a Northeast partner of Infinite Campus SIS, which provides us with critical visibility into all areas of schools. We also have extensive expertise with E-Rate funding, which helps to ensure access to affordable telecommunications, Internet access, internal connections and other essential technology services for the K-12 education community.

Zero Trust Networks: What Are They?
Zero Trust Networks: What Are They? The internet has brought a world of opportunity for businesses. It is easy for companies to reach out to consumers and offer them products or services without a physical storefront. However, this also opens businesses up to the risk...
